OneDrive
Connector Details
| Connector Attributes | Details |
|---|---|
| Name | OneDrive |
| Description | The OneDrive connector enables seamless integration with Microsoft's OneDrive cloud storage solution, facilitating efficient file management, secure storage, and effortless collaboration for both individuals and organizations. With the OneDrive connector, users can easily connect to their OneDrive accounts, gaining direct access to a comprehensive repository of documents, photos, and files. This streamlined connection supports simple file uploads, downloads, and updates, while ensuring robust version control and data synchronization across devices. Designed to enhance productivity, the connector empowers teams with secure file sharing, real-time collaboration, and automated backup features, helping organizations maintain operational efficiency, adhere to compliance standards, and drive innovation in document management. |
| Connector Type | Class B |
Features
| Feature Name | Feature Details |
|---|---|
| Load Strategies | Full Load |
| Metadata Extraction | Supported |
| Data Acquisition | Supported |
| Data Publishing | Not Supported |
| Automated Schema Drift Handling | Not Supported |
Connector Specific Configuration Details
Supported formats:
- CSV
- JSON
- XSL
- XSLX
The Empower Microsoft OneDrive connector requires registering an application in the Azure Tenant's The connector will then connect to and authenticate with the Entra ID Graph API.
Below are the steps to register and assign permissions.
Create an Azure AD Application
1. Log in to the Azure Portal
- Go to the Azure Portal and sign in with your credentials.
2. Navigate to Microsoft Entra ID
-
In the left-hand menu, click on Microsoft Entra ID.
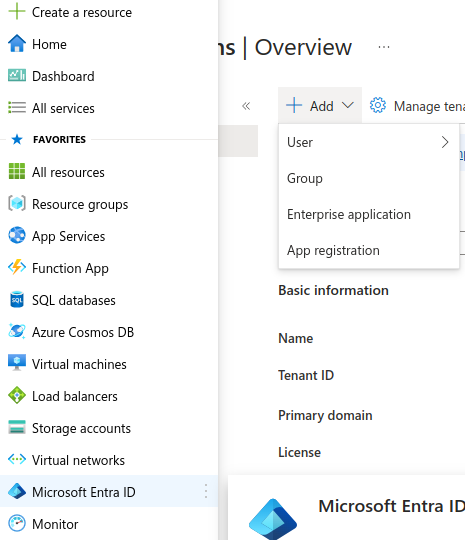
3. Register a New Application
- In the Microsoft Entra ID section, select App registrations.
- Click
+ Addat the top of the screen.
4. Configure App Registration
-
Name: Enter a name for your application (e.g.,
onedrive-graph-api-integration). -
Supported Account Types: Choose the option that applies to your application, for example:
- Accounts in this organizational directory only (Single tenant) for internal apps.
-
Redirect URI: You can leave this blank for now, or set it based on your app’s needs (e.g., a backend service might not need this initially).
-
Once everything is configured, click
Register.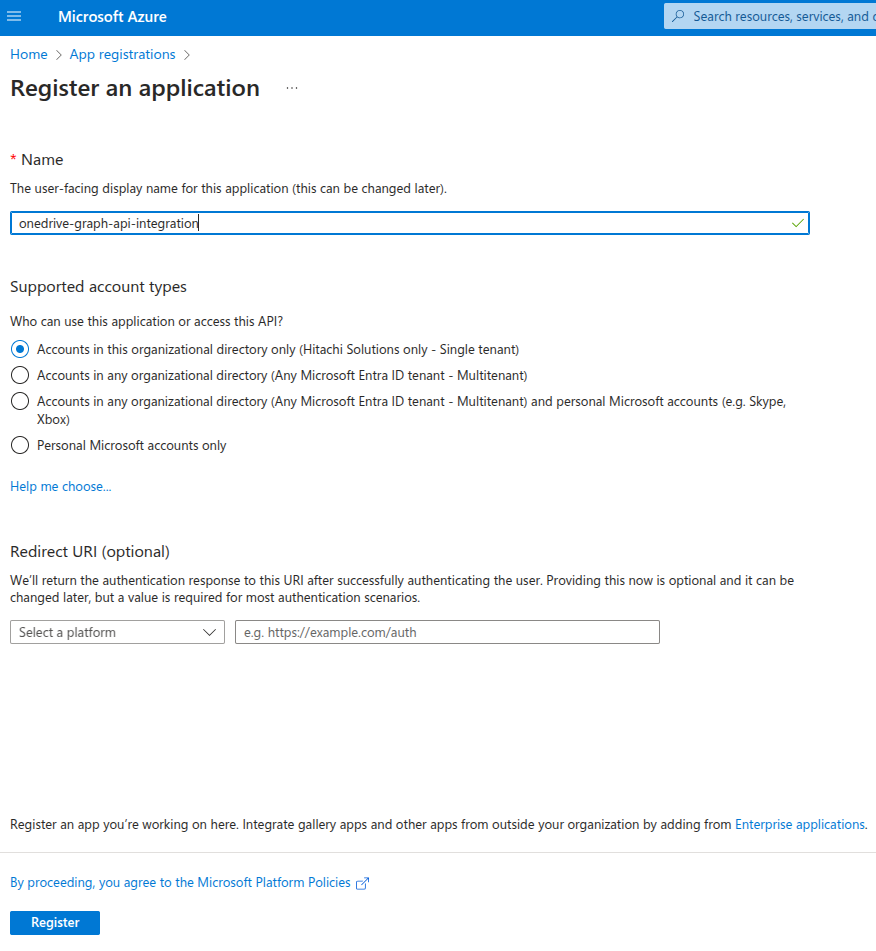
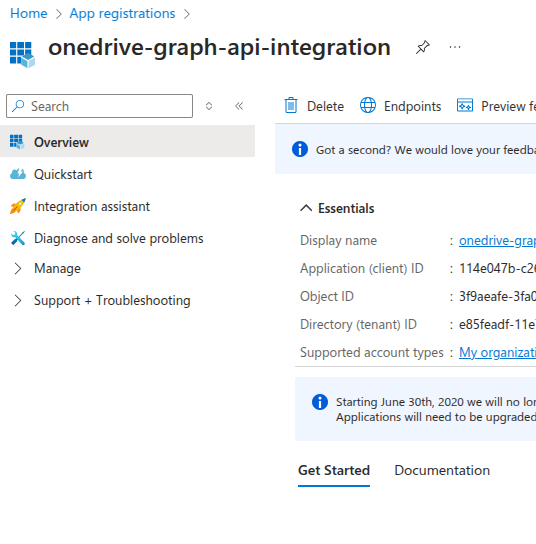
5. Save Application (Client) ID and Directory (Tenant) ID
-
After registering the application, you'll see its Overview page. Copy and save both the Application (Client) ID and the Directory (Tenant) ID. You’ll need these values for your backend configuration.
Create a Client Secret
1. Navigate to Certificates & Secrets
-
On your app’s Overview page, in the left-hand navigation menu, click Certificates & secrets.
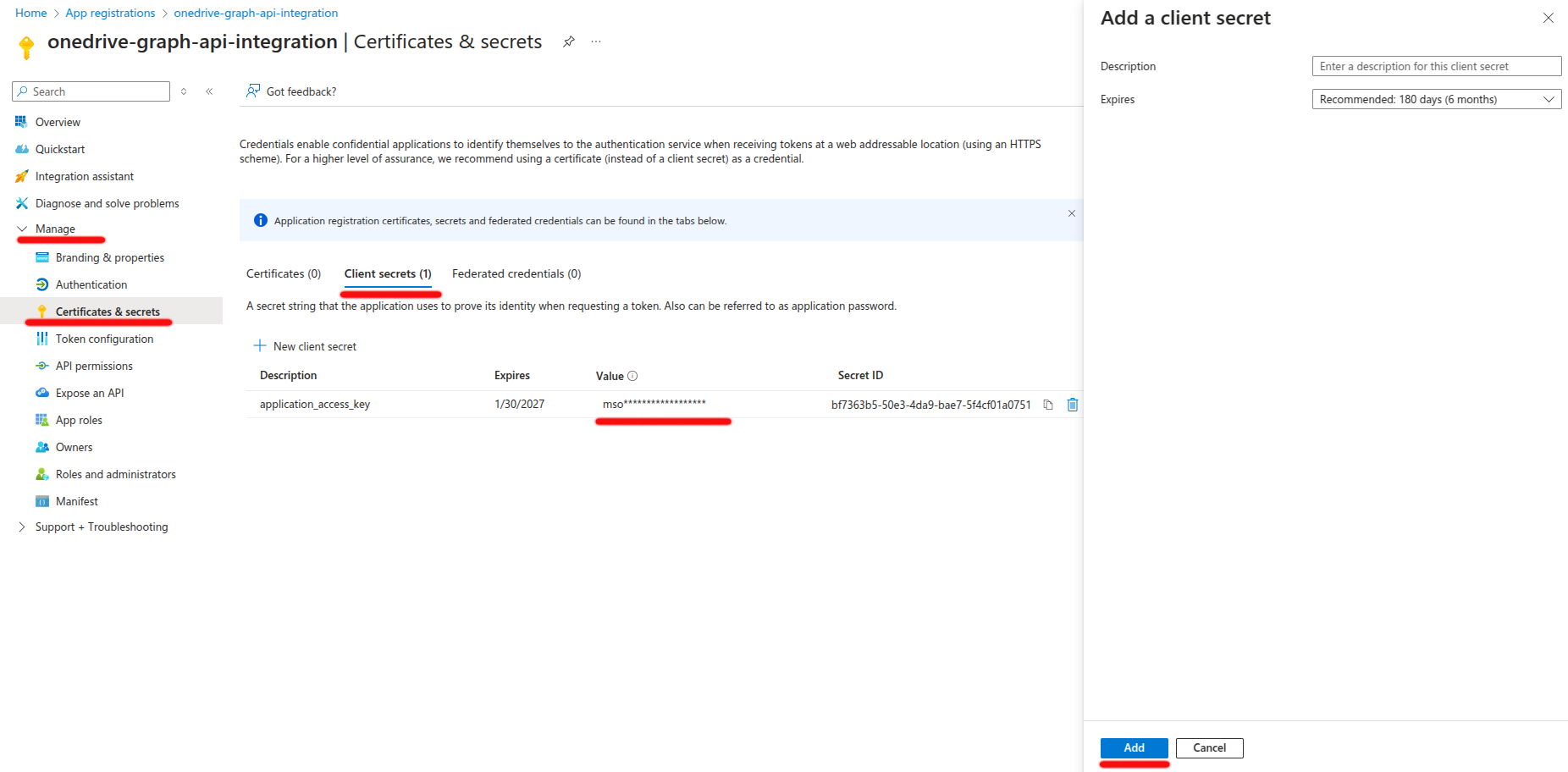
2. Create a New Client Secret
- Under the Client secrets section, click
+ New client secret. - Description: Add a description (e.g.,
application_access_key). - Expiration: Select an expiration duration (e.g., 6 months, 12 months, or 24 months). You will need to rotate this secret periodically based on the expiration.
3. Save the Client Secret Value
-
After creating the secret, copy the Value immediately. You won’t be able to view it again once you navigate away from this page.
-
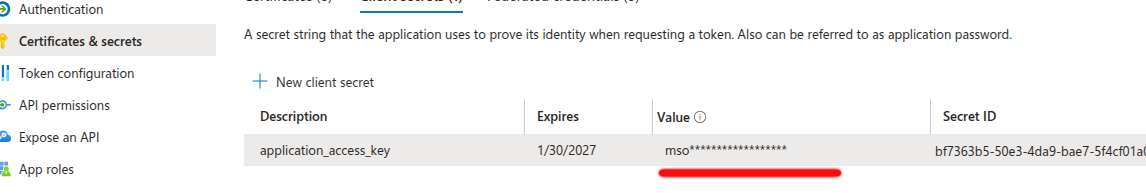
This Client Secret Value will be used later in the backend application for authentication.
Grant API Permissions
1. Navigate to API Permissions
-
In the left-hand menu, select
API Permissions.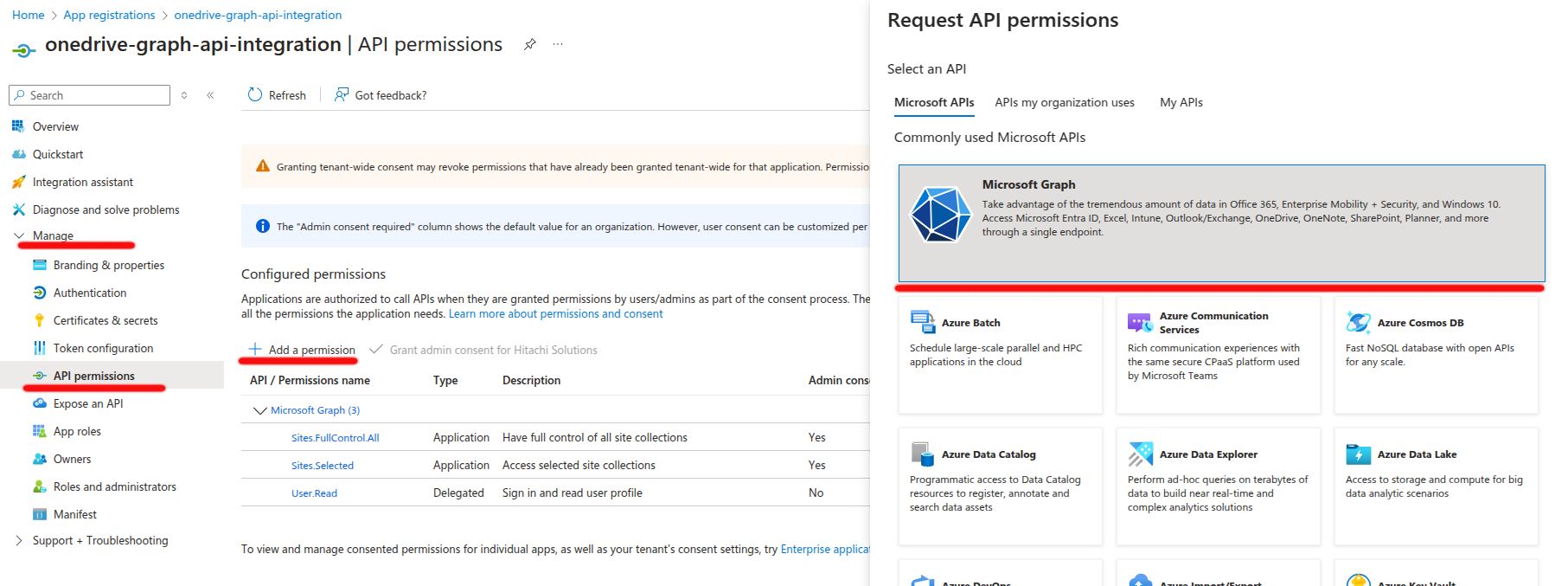
2. Add Microsoft Graph Permissions
- Click on
+ Add a permission. - In the Request API permissions window, select Microsoft Graph.
3. Choose the Appropriate Permissions
-
For the actions your backend app will perform in OneDrive, you’ll need to select
Applicationpermissions.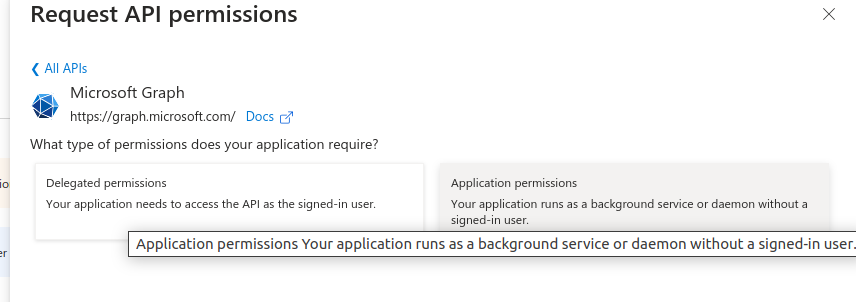
Common Permissions for OneDrive:
-
Delegated Permissions: If your app acts on behalf of a signed-in user, choose from permissions like
User.Read, etc. -
Application Permissions: If your app accesses data without a signed-in user, select permissions such as
Sites.Selected,Sites.FullControl.All, etc. (Later, we will deactivateSites.FullControl.Allwhen limited access is added.) -
Select the necessary permissions for your app and click
Add permissions.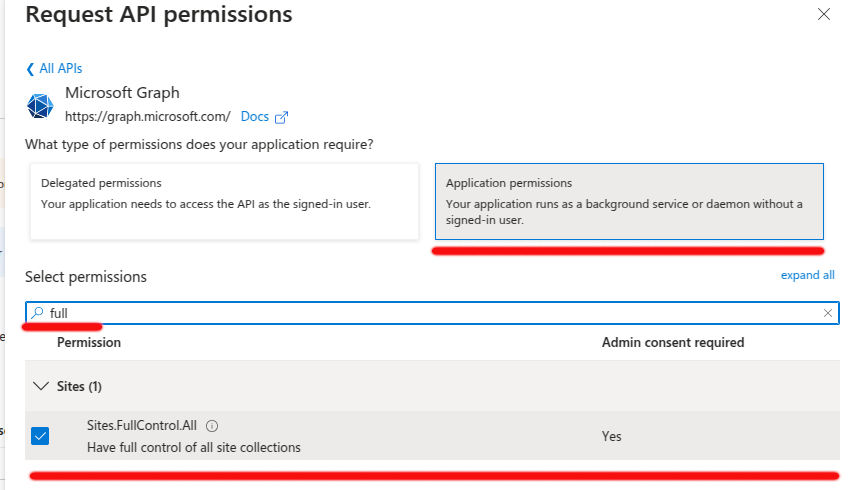
4. Grant Admin Consent (If Required)
-
Some permissions (especially Application permissions) may require Admin Consent. Click
Grant admin consent for {Your Organization}to allow these permissions.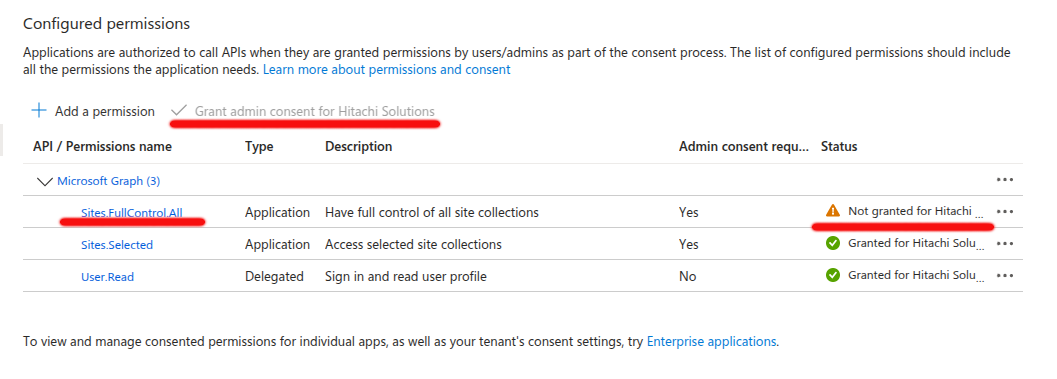
Setting Up Read Access for a OneDrive Business Account Site via Microsoft Graph API
This manual demonstrates how to grant read access to a specific user or group for a OneDrive site using Microsoft Graph API. Before proceeding, ensure you have the necessary permissions and prerequisites.
Prerequisites
-
Microsoft Graph API Permissions:
_Your application must have theSites.FullControl.Allapplication permission to modify site permissions. **IMPORTANT! It is necessary for the set read permissions after we do it - you can drop this level of access. Or create a separate application dedicated to managing permissions. **
_ Ensure these permissions are granted in the Azure portal for your registered app.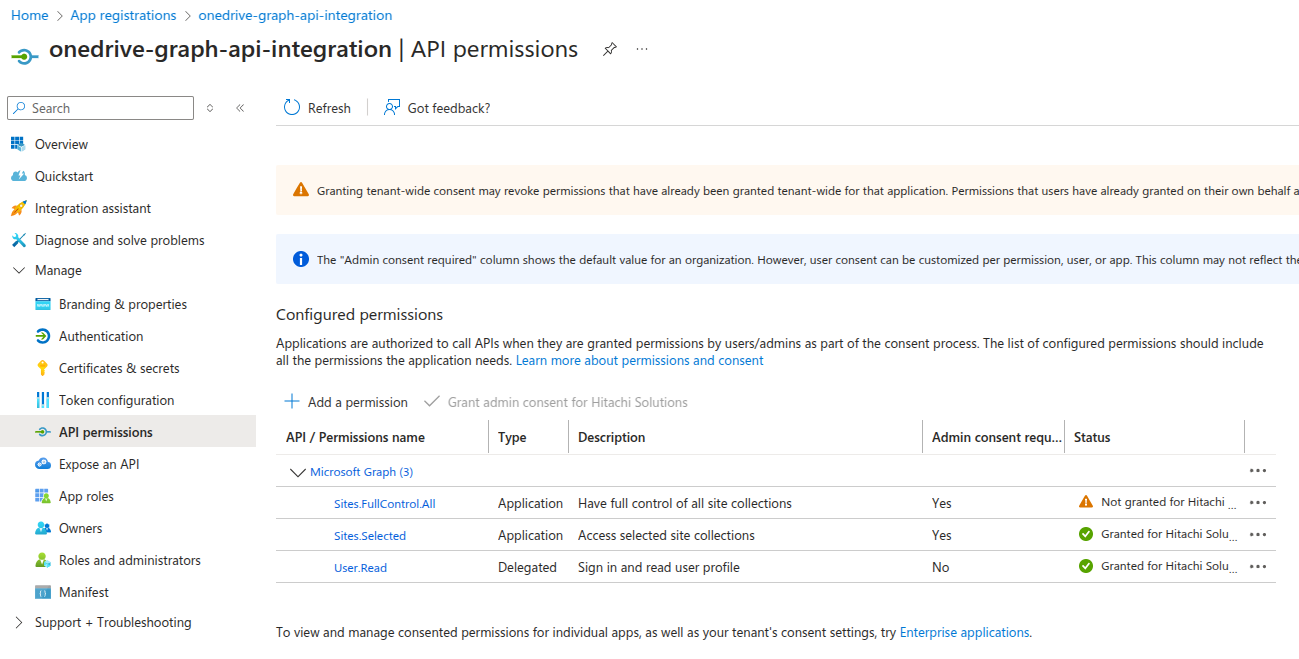
-
Authentication:
- Obtain an access token using Azure AD. Refer to Authenticate with Azure AD.
-
Tools:
- Install
curlfor making HTTP requests or use a REST client likePostman.
- Install
-
Information Needed:
- The Account ID (email) of the OneDrive where you want to set permissions.
Step 1: GetSite ID for the OneDrive account
Site ID for the OneDrive accountBefore doing any actions, we need to get a Site ID related to our OneDrive storage.
Request:
curl --location --request GET "https://graph.microsoft.com/v1.0/users/[email protected]/drive?$select=id,webUrl,sharePointIds" \
--header "Authorization: Bearer {access_token} \
--header "Content-Type: application/json"Response Example:
{
"id": "b!abcdef1234567890abcdef1234567890",
"webUrl": "https://yourdomain-my.sharepoint.com/personal/username_yourdomain_com",
"sharepointIds": {
"siteId": "12345678-90ab-cdef-1234-567890abcdef",
"listId": "87654321-ba09-fedc-4321-098765fedcba"
}
}- In this example, the
siteIdis located atresponse.sharepointIds.siteId.
Step 2: List Existing Permissions
Before modifying permissions, review the current permissions for the site.
Request:
curl -X GET \
https://graph.microsoft.com/v1.0/sites/{site_ID}/permissions \
-H "Authorization: Bearer {access_token}" \
-H "Content-Type: application/json"Response Example:
{
"value": [
{
"id": "aTowaS50fG1zLnNwLmV4dHxlNDU3NGNkOC03ZmRhLTRiNmMtOTE5Yy02NzA5YTNjNjlhMmVAZTg1ZmVhZGYtMTFlNy00N2JiLWExNjAtNDNiOThkY2M5NmYx",
"grantedToIdentitiesV2": [
{
"application": {
"displayName": "onedrive-graph-api-integration for Limited Access",
"id": "e4574cd8-7fda-4b6c-919c-6709a3c69a2e"
}
}
],
"grantedToIdentities": [
{
"application": {
"displayName": "onedrive-graph-api-integration for Limited Access",
"id": "e4574cd8-7fda-4b6c-919c-6709a3c69a2e"
}
}
]
}
]
}roles: Shows the permission level (e.g.,read,write).grantedTo****: Identifies the user or group with access.
Step 3: Grant Read Access
To grant read access, use the POST method on the /permissions endpoint of the SharePoint (OneDrive) site. Specify the principal (user or group) and the read role in the request body.
Request:
curl -X POST \
https://graph.microsoft.com/v1.0/sites/{site_ID}/permissions \
-H "Authorization: Bearer {access_token}" \
-H "Content-Type: application/json" \
-d '{
"roles": ["read"],
"grantedToIdentities": [{
"application": {
"id": "<CLIENT_ID>",
"displayName": "onedrive-graph-api-integration for Limited Access"
}
}]
}'Parameters:
roles: Specify the access level. Usereadfor read-only access.grantedToIdentities: Specify the principal (user or group) by email.
Response Example:
{
"id": "aTowaS50fG1zLnNwLmV4dHxlNDU3NGNkOC03ZmRhLTRiNmMtOTE5Yy02NzA5YTNjNjlhMmVAZTg1ZmVhZGYtMTFlNy00N2JiLWExNjAtNDNiOThkY2M5NmYx",
"roles": [
"read"
],
"grantedToIdentities": [
{
"application": {
"displayName": "onedrive-graph-api-integration for Limited Access",
"id": "e4574cd8-7fda-4b6c-919c-6709a3c69a2e"
}
}
]
}
Step 4: Verify Permissions
After granting access, verify the permissions to ensure they were set correctly.
Request:
permissionId you can get from the previous request: aTowaS50fG1zLnNwLmV4dHxlNDU3NGNkOC03ZmRhLTRiNmMtOTE5Yy02NzA5YTNjNjlhMmVAZTg1ZmVhZGYtMTFlNy00N2JiLWExNjAtNDNiOThkY2M5NmYx
curl -X GET \
https://graph.microsoft.com/v1.0/sites/{site_ID}/permissions/{permissionId} \
-H "Authorization: Bearer {access_token}" \
-H "Content-Type: application/json"Response Example:
{
"value": [
{
"id": "aTowaS50fG1zLnNwLmV4dHxlNDU3NGNkOC03ZmRhLTRiNmMtOTE5Yy02NzA5YTNjNjlhMmVAZTg1ZmVhZGYtMTFlNy00N2JiLWExNjAtNDNiOThkY2M5NmYx",
"roles": ["read"],
"grantedToIdentities": [
{
"application": {
"displayName": "onedrive-graph-api-integration for Limited Access",
"id": "e4574cd8-7fda-4b6c-919c-6709a3c69a2e"
}
}
]
}
]
}
The new permission should now appear in the permissions list.
In this step, you can remove the Sites.FullControl.All permission from your application.
However, keep in mind that doing so will also revoke your ability to manage permissions using the Microsoft Graph API. If you still need to perform actions related to permissions via the Graph API, you have two options:
- Create a dedicated application specifically for managing permissions.
- Restore the
Sites.FullControl.Allpermission to your current app.
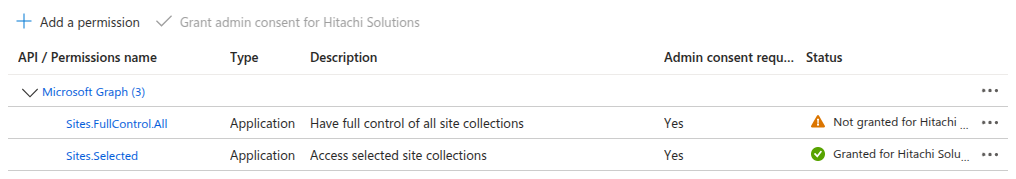
Step 4: Remove Access (Optional)
If you need to revoke access, delete the specific permission by its permission-id.
Request:
curl -X DELETE \
https://graph.microsoft.com/v1.0/sites/{site_ID}/permissions/{permissionId} \
-H "Authorization: Bearer {access_token}" \
-H "Content-Type: application/json"Response:
A successful deletion returns an HTTP 204 (No Content) status.
Python code implementation:
import msal
import requests
from pprint import pprint
class GraphAPIClient:
def __init__(self, client_id, client_secret, tenant_id, user_email):
self.client_id = client_id
self.client_secret = client_secret
self.tenant_id = tenant_id
self.user_email = user_email
self.authority = f"https://login.microsoftonline.com/{tenant_id}"
self.scopes = ["https://graph.microsoft.com/.default"]
self.access_token = self._get_access_token()
self.headers = {"Authorization": f"Bearer {self.access_token}"}
self.site_id = self._get_onedrive_root()
def _get_access_token(self):
app = msal.ConfidentialClientApplication(
self.client_id, authority=self.authority, client_credential=self.client_secret
)
token_response = app.acquire_token_for_client(scopes=self.scopes)
if "access_token" in token_response:
return token_response["access_token"]
else:
raise Exception(f"Could not get token: {token_response}")
def _get_onedrive_root(self):
url = f'https://graph.microsoft.com/v1.0/users/{self.user_email}/drive?$select=id,webUrl,sharepointIds'
response = requests.get(url, headers=self.headers)
if response.status_code == 200:
try:
return response.json()['sharePointIds']['siteId']
except KeyError:
raise Exception("Could not find 'siteId' in the drive information.")
else:
raise Exception(f"Error {response.status_code}: {response.text}")
def make_api_call(self, endpoint, request_type="GET", json_data=None):
if request_type == "GET":
response = requests.get(endpoint, headers=self.headers)
elif request_type == "POST":
response = requests.post(endpoint, headers=self.headers, json=json_data)
else:
raise ValueError("Unsupported request type")
if response.status_code == 200:
return response.json()
else:
print(f"Error {response.status_code}: {response.text}")
return None
def get_site_permissions(self):
"""Get the permissions for a SharePoint site."""
permissions_info_url = f"https://graph.microsoft.com/v1.0/sites/{self.site_id}/permissions"
permissions_info = self.make_api_call(permissions_info_url)
print(f"permissions: {permissions_info}")
def get_site_permission(self, permission_id):
"""Get the permissions for a specific SharePoint site permission."""
permissions_info_url = f"https://graph.microsoft.com/v1.0/sites/{self.site_id}/permissions/{permission_id}"
permissions_info = self.make_api_call(permissions_info_url)
print(f"permissions: {permissions_info}")
def post_site_permissions(self):
"""Post new permissions to a SharePoint site."""
json_data = {
"roles": ["read"],
"grantedToIdentities": [{
"application": {
"id": self.client_id,
"displayName": "onedrive-graph-api-integration for Limited Access"
}
}]
}
permissions_info_url = f"https://graph.microsoft.com/v1.0/sites/{self.site_id}/permissions"
permissions_info = self.make_api_call(permissions_info_url, "POST", json_data)
print(f"permissions POST: {permissions_info}")
if __name__ == "__main__":
client = GraphAPIClient(
client_id='11testb-test-42f9-teest-teetsteset',
client_secret='mteste2ddNUUttest6WtestLqDtesttest',
tenant_id='test-11e7-47bb-test-43b9test96f1',
user_email='*****@******.***'
)
pprint(client.get_site_permissions())
client.post_site_permissions()
client.get_site_permissions()Share access to the different user(s)/group(s)
If you want to collect data from multiple users, you can optionally create a dedicated folder for each user and grant them or their group access.
Once access is shared,
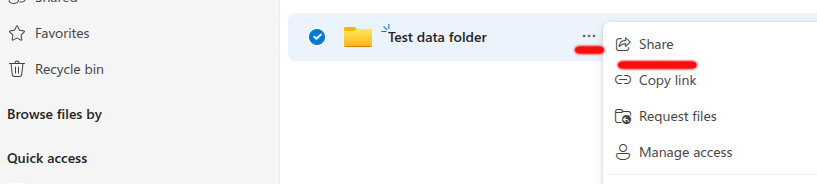
the users will receive a notification and can upload files to that folder.
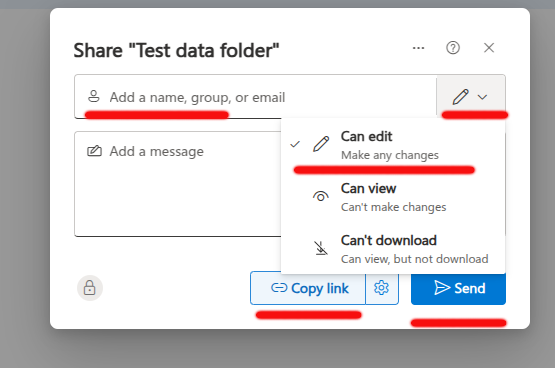
To share the folder, simply copy the link from the user interface. Afterward, run metadata extraction to process the new files.
Mandatory conditions for the OneDrive static CSV files:
CSV files:File Format
The connector is designed to handle files only in CSV format. Ensure all files used or processed by the system are in .csv format for compatibility with the connector.
Use of Separator
Always use a comma , as the separator in your data files. This ensures consistency and compatibility across different systems and processes.
Encoding Standard
Ensure that all files are saved and processed using UTF-8 encoding. This is crucial to maintain character integrity, especially when working with international data or special characters.
File Movement or Renaming
When you move or rename a file, it is essential to update the associated metadata. This ensures that all references to the file are accurate and that no processes relying on this data are disrupted.
Replacing a File Without Dropping
If you are replacing a file but not dropping and creating a new one, you can continue to use the same table name. This allows for a seamless transition and minimal disruption to the existing data structure.
Dropping and Creating a New File
When you drop and create a new file with the same name, it is necessary to update the metadata. This ensures that the system properly references and recognizes the new file, preventing potential issues with outdated information.
Configure Your Backend Application
Now that you have the necessary credentials, you can configure your connector to authenticate and interact with OneDrive via the Microsoft Graph API.
Collect Variables:
- Tenant ID: The Directory (Tenant) ID you saved earlier.
- Client ID: The Application (Client) ID you saved earlier.
- Client Secret (App secret): The Client Secret value you created.
- Account ID (email): The Account Email you got earlier.
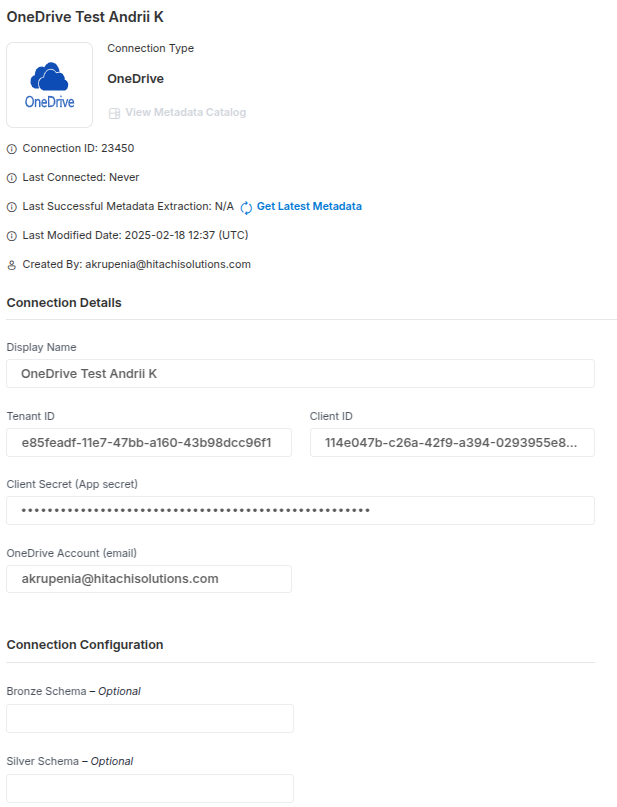
Permissions Requirements
The registered app will need Graph API Sites.FullControl.All, Sites.Selected permissions for each endpoint for the type of data required to extract into Empower. Below is the minimum requirement
| Resource | Permission | Short Description | Admin consent required | Development Access? |
|---|---|---|---|---|
| Application | Sites.FullControl.All | Have full control of all site collections | Yes | Yes |
| Application | Sites.Selected | Access selected site collections | Yes | Yes |
Updated 4 months ago
