Workday
Connect Empower to Workday
Workday Connection
To set up your Workday integration, first, connect your Workday instance to Empower.
Introduction - Workday on Empower
The Workday connector uses the Workday Web Services, RaaS, and REST API. Workday recommends using an Integration System User (ISU) for integration using third-party services like Empower.
Both the Workday Web Services and RaaS require basic authentication. REST API requires an additional OAuth client setup.
Workday REST API is used to work with custom objects in your Workday instance. If this is required by your use case, indicate that you are using custom objects. See instructions on how to register a Workday API client here.
Workday Connection Properties
Connection field | Description |
|---|---|
Connection name | Give this Workday connection a unique name that identifies which Workday tenant it is connected to. |
Login name | This should be the login name for the ISU. |
Password | This should be the login password for the ISU. |
Tenant | Tenant is found in the URL when you are logged into Workday. For example, if the URL of your Workday tenant is |
API WSDL URL | This URL is used to generate schema and forms the base URI for every API requests. Find out how to obtain this URL from this Workday article. The default is |
Client ID | The Client ID obtained from the View API Client page. |
Client secret | The Client Secret obtained from the View API Client page. |
Authorization endpoint | Authorization endpoint of the API Client you created to connect to. |
Token endpoint | Token endpoint of the API Client you created to connect to. |
CustomReportURL | The XML Link to a RaaS report created below. See Accessing Reports as a Service. |
Register Integration System User
We do not recommend using a user account of a worker to run integrations. There are a few reasons for this.
Firstly, all operations performed by the integration will be logged under this worker instead of one dedicated for integration and workflow processes.
Furthermore, if this worker security profile changes, or if the worker is terminated, integrations that rely on this worker's user account will no longer work.
The recommended approach to access web services is through an Integration System User (ISU) account. For security reasons, each ISU should be restricted to a single integration system (like Empower).
The ISU should have all the permissions needed to perform the required actions for your integration scenario. When building recipes, you may encounter a 403 error, it means that the ISU does not have sufficient permission for the action.
Create an Integration System User
Step | |
|---|---|
1 - Create Security Group | Access the Create Security Group task and create an Integration System Security Group. |
2 - Grant Domain access to Security Group | To grant the security group access to the domains required by your integration, follow these steps for each domain:
Additionally, grant
Next, access the Activate Pending Security Policy Changes task and activate these changes. |
3 - Create ISU account | Access the Create Integration System User task and configure a Workday user account for the integration. Keep the Session Timeout Minutes default value of 0 to prevent session expiration. An expired session can cause the integration to time out before it successfully completes. Select the Do Not Allow UI Sessions checkbox if you wish to prevent the integration system user from signing in to Workday through the UI. To avoid integration errors caused by expired passwords, Workday recommends that you prevent Workday user passwords from expiring. Access the Maintain Password Rules task and add the integration system user to the System Users exempt from password expiration field. |
4 - Assign Security Group to ISU | As a related action on the Workday user, select Security Profile > Assign Integration System Security Groups. At the Integration System Security Group to Assign prompt, select the security group that you created. Access the View Integration System report and access the Connector or Studio integration. Select Workday Account > Editas a related action on the integration system. On the Edit Account for Integration System task, select the ISU account that you created. |
Setting the Integration Language
In the Global Preferences area, select a preferred locale and display language for the integration system user. These settings control what language Workday uses for the integration data. An outbound integration sends data in the preferred language and an inbound integration saves data in the preferred language.
If you leave these fields blank, Workday uses the default locale and display language for integration data.
Find out more about setting up an ISU here.
Register API Client
This step is required. The Workday connector uses the Workday REST API, which uses an OAuth 2.0 for authentication. You need to register an API Client to allow connection to the REST API.
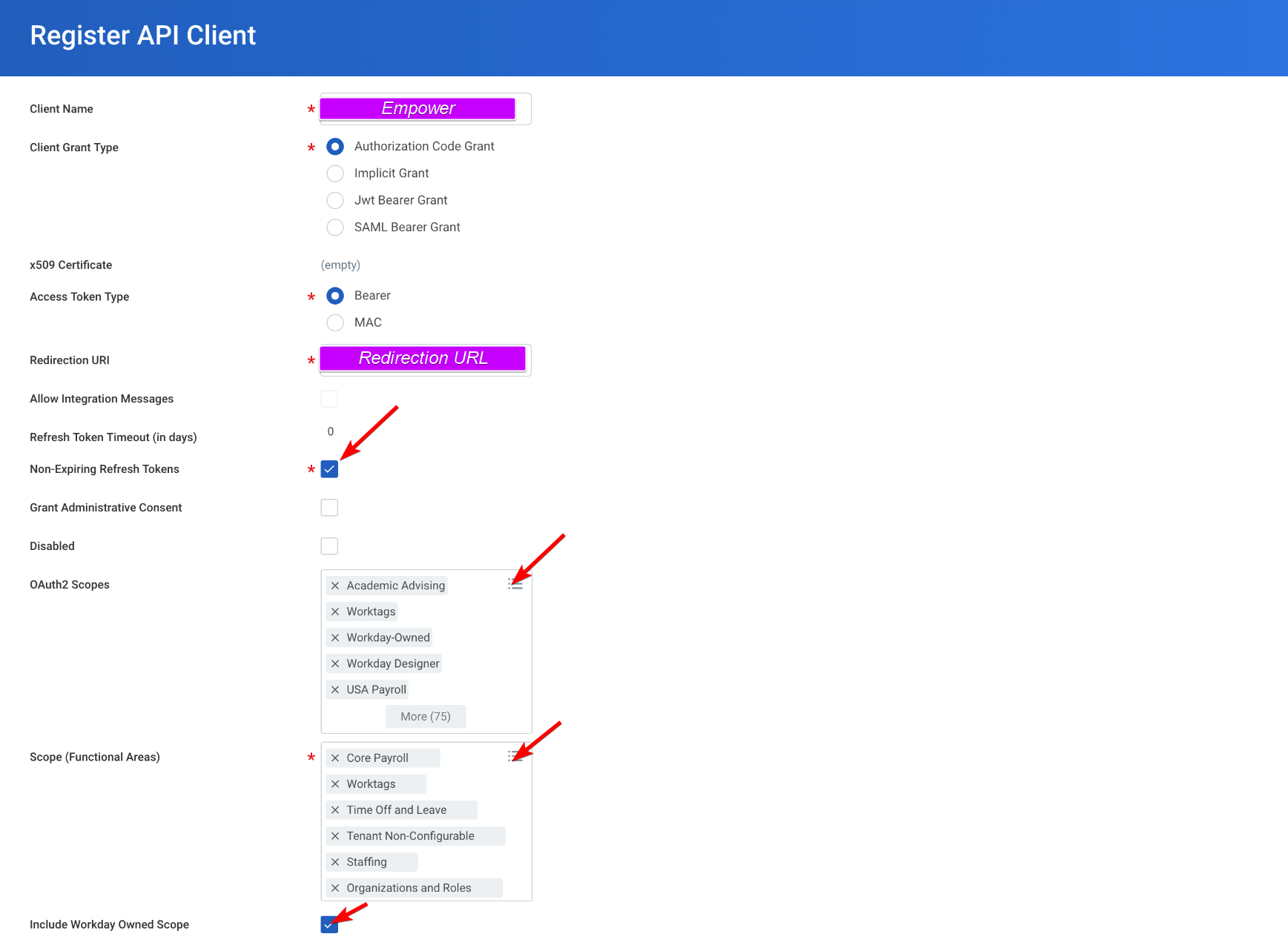
Registering a new client
Navigate to "Register API Client" in your Workday instance.
- Select Authorization Grant
- Use
https://localhost:33333as the Redirection URL - Add the necessary scope you wish to grant access for (or add all functional areas)
Required ScopesIn the Scope section, be sure enable the Custom Objects > System scope. The driver uses system endpoints to list views and columns.
Also, be certain to check the Include Workday Owned Scope box.
Remember to save the Client ID, Client Secret, Authorization Endpoint and Token Endpoint. They will be required for the Workday integration connector setup.
Accessing Reports as a Service
Empower supports reading reports that have been exposed through Workday Reports as a Service (RaaS). Workday does not have a built-in way for the driver to determine which reports have been exposed via RaaS, so you must create a custom report to use this feature:
- Open the Create Custom Report form.
- Name the report Reports as a Service.
- Enter Advanced for the report type.
- Select Enable As Web Service.
- Clear Optimized for Performance.
- Enter All Custom Reports for the Data Source.
After the report is created, you need to add a few columns and filters:
- In Fields
- For the first column, enter Report Name.
- Add a second column and enter Web Service Namespace.
- Add a third column and enter Report Owner.
- Add a fourth column and enter Brief Description.
- Make sure all columns have the primary business object as their Business Object. The primary business object has the name Custom Report and should have a box-and-arrow icon beside it. If the icon is an ellipsis (...) instead, then click menu, select Primary Business Object and then Custom Field.
- Open the Filter tab and create a new filter. Enter Web Service Namespace as the field and is not blank as the Operator.
- Add a second filter. Enter Current User as the field, in the selection list as the Operator, Value from Another Field as the comparison type, and Authorized Users as the comparison value.
- Click OK to save the report. If Workday displays any warnings then click OK again to dismiss them.
The final step is to find the URL associated with the report. This URL is used to set the CustomReportURL connection property.
- Open the newly created report.
- Click the ellipsis (...) button beside the report title in the upper-left corner of the screen
- Find the Web Services tab within the pop-up. You may have to scroll down inside the pop-up to see it.
- Hover over it and select View URLs.
- Copy the Workday XML link.
Updated about 2 months ago
